Comparing Symmetric and Asymmetric Encryption: Understanding the Differences and Use Cases
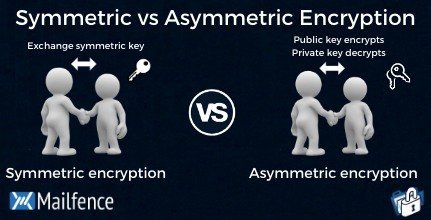
In the area of cybersecurity, encryption functions as a secret language, keeping our digital communications private and safe. There are two major forms of encryption: symmetric and asymmetric. Let's take a deeper look at each one to see how they function and where they excel. Symmetric encryption is similar to sharing a secret with someone you trust. Assume you and your best buddy share a unique code that only you two understand. When sending a secret message, use this code to jumble it. Your buddy then uses the same code to decipher and read the message. That is how symmetric encryption works: it utilizes the same key to lock and unlock the communication. It is extremely quick and efficient since it is similar to two parties exchanging a secret handshake. But there's a catch: you must discover a means to safely communicate your secret key with your pal. If someone else gets hold of it, they can read all of your private communications.
In contrast, asymmetric encryption is analogous to having two magic keys: one for locking and one for unlocking. Assume you have a unique lock that only your friend's key can open, and vice versa. You can share your magic lock with the entire globe, but only your friend's magic key will unlock it. This is the fundamental concept underpinning asymmetric encryption. You have two keys: one public, which you share with everyone, and one private, which you retain to yourself. When sending a secret message, you utilize the recipient's public key to encrypt it. Only the receiver with the appropriate private key may unlock and view the message.It's similar to having a digital signature that only you can generate and validate. Asymmetric encryption is ideal since you don't have to worry about exchanging secret keys; instead, you just share your public key with anyone who want to send you a secret message.
Symmetric encryption is like a speed racer for encryption schemes. It's incredibly quick and ideal for encrypting enormous volumes of data in real time. That is why it is commonly utilized in applications such as safe online transactions and online movie streaming. When you make an online purchase, you want your payment information protected swiftly and securely; this is where symmetric encryption comes in useful. It is also useful for encrypting files on your computer and safeguarding communication between devices in the Internet of Things (IoT). Symmetric encryption is known as the "workhorse" of encryption systems because to its speed and efficiency.Asymmetric encryption, similar to cybersecurity guardian angels, provides an extra layer of safety in certain scenarios. Its superpower is digital signatures, which may be used to verify the legitimacy of digital documents. This is critical for secure email communication and software download integrity. Asymmetric encryption is especially effective in secure communication across untrusted networks such as the internet because it eliminates the necessity for secret key exchange, making it perfect for establishing safe connections between people who have never met in person.
To summarize, symmetric and asymmetric encryption are like two sides of the same coin, each with unique strengths and drawbacks. Symmetric encryption is quick and effective, making it ideal for routine operations such as online shopping or encrypting computer data. Asymmetric encryption, on the other hand, adds an extra degree of protection by supporting digital signatures and safe communication over untrusted networks. Understanding the distinctions between these two methods of encryption is critical for keeping our digital world safe and secure. So, whether you're sending a secret message to your closest friend or making an online purchase, encryption ensures your information remains private and safe.
Posted using Honouree